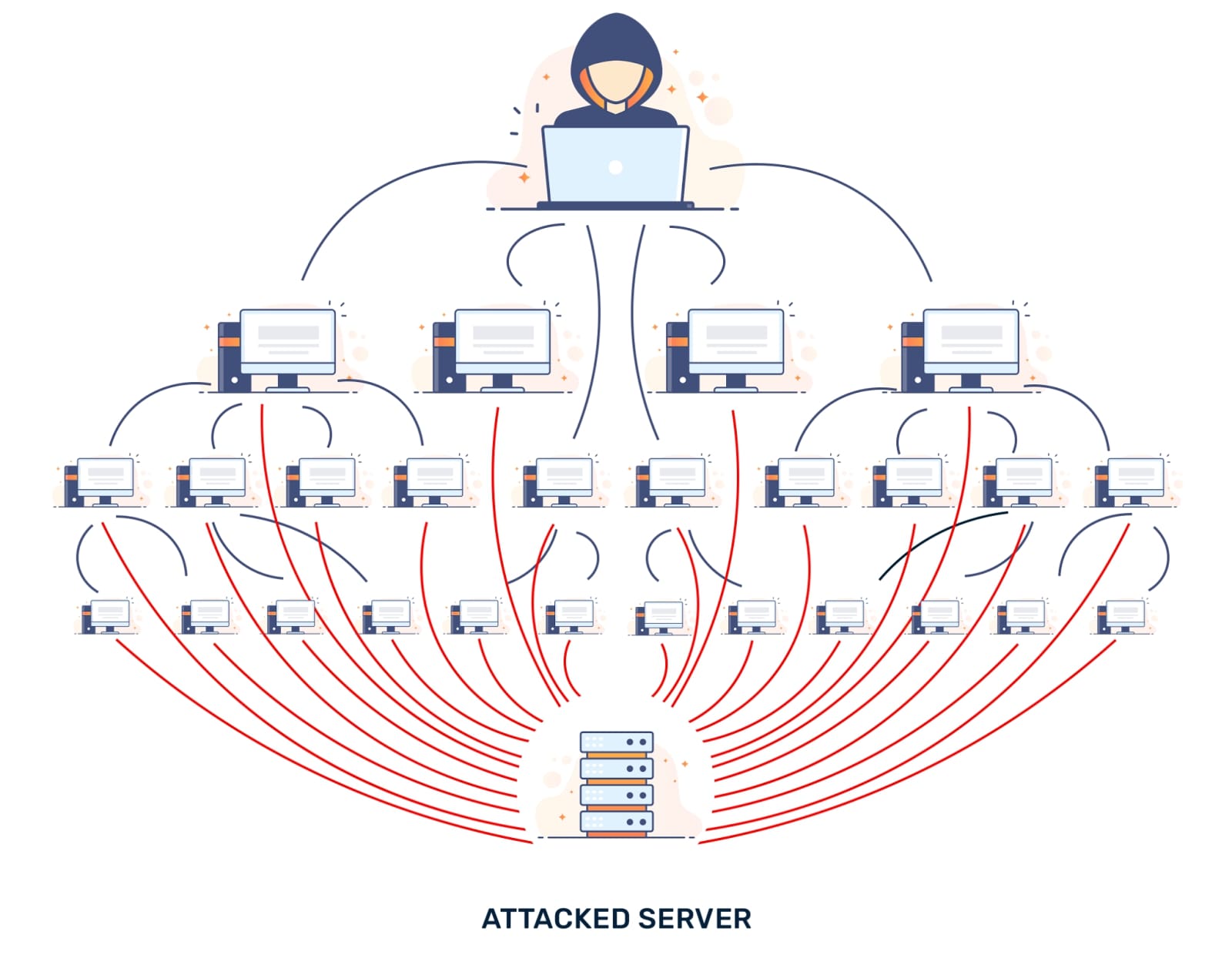
Ladies and gentlemen, I suppose that most of you have heard of something called a DDoS attack, or a distributed denial of service attack. If not (and even if you do), let me describe it as simply as possible for you.
In the digital world, a DDoS attack is a crowd of “visitors” from all over the Internet who suddenly start harassing your server with queries, bringing it to a state of paralysis. Such inquiries, my dear, are not polite letters, they are rather shouts that reach the server from every direction, and at the same time.
Nowadays, when the Internet is like the Wild West, full of unknown threats and enemies, DDoS attacks are becoming more and more popular. We become easy targets for those who have access to the technology and tools that make such an attack possible. For a small fee, you can create digital disruption on a scale that is hard to imagine. You can thwart the plans of even the largest institution, regardless of where it is located.
The Effects of a DDoS Attack – Chaos, Reputational Damage, and Financial Losses
First, there is chaos. A break in work is like an unexpected fire in a cigar factory. Production comes to a standstill, people are running in different directions, and you’re sitting alone with a cigar in your hand, wondering what actually happened.
Then, we have the loss of trust. Imagine that you are a whiskey producer. If your distillery closes, people will start to wonder if your product is really as good as you say. In addition, processes such as purchases or registrations are starting to resemble chariot races – they are devoid of control.
Last but not least, are financial losses.
DDoS attack – filter network traffic like gold through a sieve
The latest anti-DDoS solutions are like watchdogs on towers, using state-of-the-art scopes to observe movement on the horizon. They use something called machine learning. These intelligent algorithms analyze network traffic and then determine the traffic pattern and its dynamics, allowing them to detect any anomalies.
These solutions are like a solid fortress, providing protection at both the network and application levels. Only a few DNS records change, and traffic filtering begins. All HTTP/HTTPS traffic is carefully passed through a filtering layer that examines every packet and query like a detective at a crime scene.
Unwanted elements trying to sneak through are immediately filtered out, so only clean, uncontaminated traffic reaches your website.
So here we are, dear ones, everything you need to know about the effects of a DDoS attack, and you already have the knowledge of how you can defend yourself against the threat. Remember, however, that you always have to be vigilant and prepared for the unexpected. Because while we may have the best guards and the safest fortresses, we never know when the next attack might come.
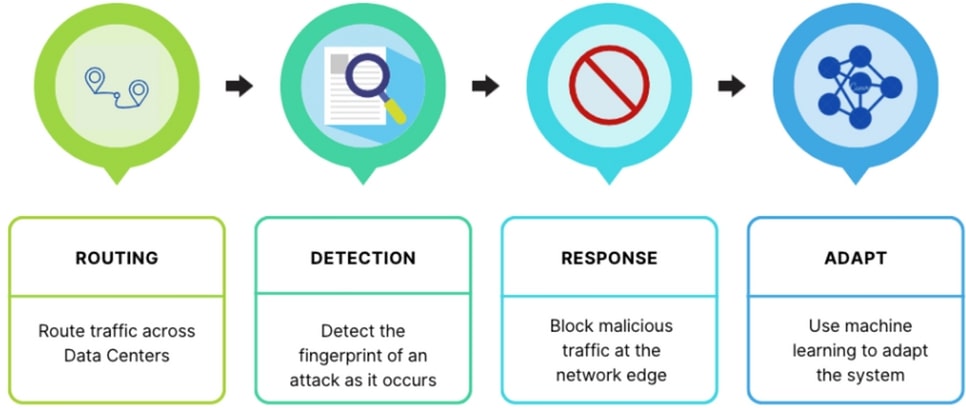
What DDoS attacks can you block with anti-DDoS solutions?
So, you’re curious about what types of attacks can be blocked, right? It’s a bit like asking what bandits can be caught. So I will present you with a list of those that you can easily catch with our help:
- TCP SYN+ACK — these are the ones who try to get into your bank through the main door, telling the guard that they have a meeting with the director.
- TCP FIN — they try to flee the scene of the crime by closing the door after themselves.
- TCP RESET – This is a bit like a bandit trying to reset the clock at the cash register.
- TCP ACKs — these are the ones who try to get into your bank by pretending to be a courier.
- TCP Fragment – a bandit who tries to smuggle diamonds by breaking them into small pieces.
- UDP Flood – A criminal who is trying to flood your gold mine to force you to leave.
- Slowloris – A bandit who moves very slowly, trying to avoid detection.
- Slowpost — He sends you threatening letters, but he does it so slowly that by the time you get the letter, he’s already a long way off.
- Local File Inclusions – Tries to steal your secrets by eavesdropping on your conversations.
- HTTP GET Flood – These are the ones who try to flood your office with letters asking for information.
- HTTP POST Flood —They try to flood your office with letters with information you didn’t want.
- HTTPS Attacks — They try to attack your vaults using data they’ve obtained illegally.
- SQL Injection – a bandit who tries to break into your bank using secret codes.
Remember that the list of attacks we can protect ourselves from is long, but it is not a complete list of all potential threats. Although we know most of the tricks that cybercriminals have up their sleeves, they can always invent new methods to surprise us. You should always be ready for the unexpected and have a plan in case something goes wrong.
ITH Security comes to the rescue – a real sheriff in the digital, wild west. We perform vulnerability scans of IT infrastructure – this is nothing more than searching for hidden tunnels that could be used for illegal penetration.
WAF – what is a Web Application Firewall and how does it work?
Do you remember the guards on the towers? Then meet WAF, or Web Application Firewall, a real hero in the digital world.
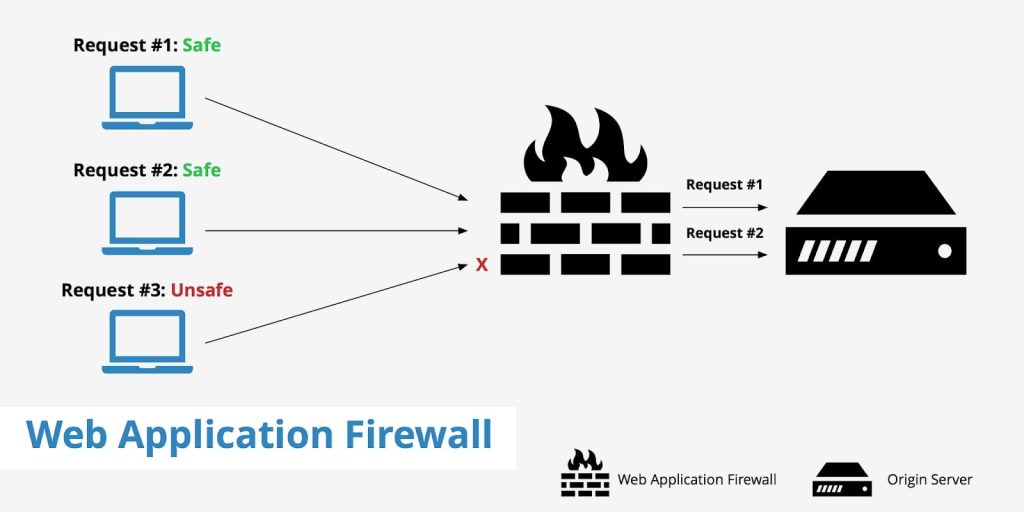
It’s like hiring Sherlock Holmes to guard your digital gates. It analyzes every incoming HTTP/HTTPS request and every application response, leaving no room for any irregularities. This protects us from nasty attacks like SQL injection, Cross-Site Scripting, and even unfamiliar threats like a zero-day exploit. This is all thanks to mysterious algorithms that, like Sherlock’s deductive skills, learn on the fly to always be one step ahead of cybercriminals.
IoT – how to take care of our data in the world of “smart” devices?
Now let’s move to another world, the world of the Internet of Things, or IoT. It’s like a small, growing town, full of modern smart devices that can connect to the network. But as you know, even the most optimistic place has its dark corners. These modern devices can not only be fantastic helpers in everyday tasks, but also a delicacy for cybercriminals.
Remember – our data is like our homes, we must do everything to protect it from uninvited guests.
Anti-DDoS Optimal Protection for Your Website
You should focus on several aspects to be sure that your website is optimally protected.
- Link – By using your bandwidth and the traffic you generate, you can determine how intense your DDoS protection should be. This is the basis for choosing the right plan.
- Websites/Domains – The amount of domains you intend to protect affects the scope and type of protection you need.
- Security – Security is multidimensional. You need to take care of DDoS protection, content protection, blocking unwanted IPs (or countries), anomaly detection, and protection at different network layers.
- SSL – In this era of increasing number of attacks, SSL protection is essential. You need to make sure that your solution supports the latest version of SSL software, protects against SSL vulnerabilities, and can deal with different types of attacks.
- Performance – Of course, protection shouldn’t come at the expense of performance. Solutions such as CDN and file caching will help keep your website fast and efficient.
- Web Application Firewall (WAF) – A WAF is an additional layer of protection. It protects against a number of attacks, such as XSS, SQL Injection, attacks on popular platforms such as WordPress or Joomla, and also allows you to personalize the rules.
- Analytics and settings – It’s good to be in control of what’s going on. Access to statistics, API, attack notifications, the ability to set your own error pages, and load balancing are just some of the features that should be available.
Leave a Reply